Check out the new video from our parent organisation. (Sorry for the bitable banners)
Tag Archives: software
How far will you let technology take over?
Lately I have had conversations with quite a few businesses that are all adopting technology at various levels. Some are all for it and adopt the latest and greatest systems to make their workload more manageable, others keep what they see as a safe distance between them and technology.
I must admit even the smaller things, like I always used to have a pocket diary and a desk diary in the past and used them all the time. Now I have a smart phone and tablet and they hold my diary and to do list all in the cloud and they ping and pop to remind me of what the next event in my life is. A small change you may say, but a massive one for some business owners and personnel.
Other things such as keeping documents on a drive that automatically backs up and then having another backup of key areas in the cloud as well, just in case. Before that I had paper lever arch folders all along a large shelf that used to dispense them on my head as I passed by on many occasion. Less clutter I suppose.
Technology reliance
So am I too reliant on technology or is this OK and where do you draw the line?
What brought this post on was an article on the BBC technology news page that stated that Samsung have warned against talking in front of some of their smart TV’s as they listen for commands to be voice activated and record conversations and share them to third parties. I was and am shocked that this could even be happening and I am for new technology and where it can take us. Listening, recording and sharing a conversation that I am having in my own living room is just not on. It is a stage too far. We are all told that security is all down to us and we need to take care and not share the wrong info with the wrong people and keep our passwords secure. Then I read this.
I feel that the use of technology is great and has revolutionised the way I operate and I would say mostly for the better. But I am also not keen on the larger companies trying their arm with stuff like this. No way. A rethink is needed here and I assume that Samsung and others will realise this and make changes.
Should we be frightened?
This should not scare us away from anything technological as there are problems with every method you have of working and it is not always the medium that is causing the issues. So adopt what you feel comfortable with but don’t shy away from trying new ways of handling your daily tasks and workloads. If need be get advice and move a step at a time. Years ago everything was posted and then faxed, and then emailed. Even that is getting superseded by instant messaging systems.
Who knows where we will be in a few years’ time. Breathe and move on….
What do you use to browse the shops?
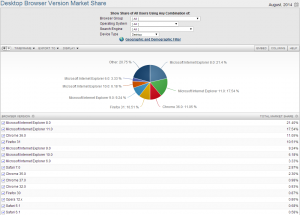 Imagine the internet as a large series of shop windows from all over the globe. We all need a method of browsing through them, and finding and buying information or physical goods. So, what do you use as your internet browser?
Imagine the internet as a large series of shop windows from all over the globe. We all need a method of browsing through them, and finding and buying information or physical goods. So, what do you use as your internet browser?
For a long time, Microsoft had the market sewn up – as it built its browser, Internet Explorer, into the Windows OS – and so everyone used it without giving it much thought. If it works, then why change? Well, people did change – and they did it because they felt that IE wasn’t doing a good enough job of displaying the web to you, the customer, in an accurate and intuitive way. So various other browsers have been developed, and the majority run quite happily on the Windows platform.
I have tried various browsers over the years, mainly on my Windows based machines – and now more recently on my Android based devices – and find each browser to have its own set of positives and negatives. The picture above shows a rough breakdown of internet browsers in use at the moment, mainly for desktop machines running Windows.
So what do we look for?
So what do we look for in an Internet Browser? Are they all the same? Should we be bothered?
It is a personal decision, and you should use which ever one you feel most comfortable with, but be aware of the following areas: –
- Rendering of web content. Some browsers display web content much faster than others, and for you the end user that saves time and frustration waiting for web pages to load.
- Security features. Each browser claims a set of security features that allow for secure connections and more secure shopping etc. Check them out and make sure you are happy with what they are offering and how they are handling it.
- Cookie handling. Browsers each handle cookies, which are small text based files that store some details of your path through the Internet. Most cookies are time saving and harmless, but some are Malware – and can cause popup windows etc. Check what settings each browser allows you to change to get the level of security that suit you and your business.
- Some browsers allow you to save a list of your open tabs and create a snapshot of where you have been – this is then available when you leave your desktop machine and go mobile. Chrome for example lets me see the tabs I was looking at when I was seated at my desk – and this all leads to an easier work environment.
- The look and feel. Again, this is a personal choice, some of it is down to the look and feel of the browser. You may find some are easier than others to use and navigate around. They all constantly update themselves, and so just as you think you have sussed the settings and where to find stuff they can change it all. But, hey, that’s computers and applications for you.
Why not let us know what browser you use, and why you use that one. Give us your experiences of browsers you have tried and why you moved on to others.
We look forward to reading your posts.
Hack in the box!
 On average 30,000 websites are hacked every day*, 200,000 new malicious programs/viruses are detected every day**. Google recently reported that they detect 9,500 websites/day infected with malware used for drive-by download attacks, where the victim only has to browse the site to become infected, and 4,000 of these sites are legitimate company websites. Small business have been a target for cyber criminals for a few years now, because they are an easier target due to their lack of budget and expertise. Is your network as secure as it can be from hackers? Are you sure? Or are you helping cyber criminals distribute malicious programs to your customers, friends and family, even if you’re computers are just acting as a base of operations for attacking and infecting others.
On average 30,000 websites are hacked every day*, 200,000 new malicious programs/viruses are detected every day**. Google recently reported that they detect 9,500 websites/day infected with malware used for drive-by download attacks, where the victim only has to browse the site to become infected, and 4,000 of these sites are legitimate company websites. Small business have been a target for cyber criminals for a few years now, because they are an easier target due to their lack of budget and expertise. Is your network as secure as it can be from hackers? Are you sure? Or are you helping cyber criminals distribute malicious programs to your customers, friends and family, even if you’re computers are just acting as a base of operations for attacking and infecting others.
* Sophos Labs Report ** Kaspersky Labs Report
It is estimated that cybercrime costs the world’s economy between $1 – 3 trillion per year.
Many businesses around the world have been struggling financially for a number of years, but sadly the underground hacking economy seems to be alive and well. In July of 2013, the FBI charged two Russians for hacking into US Financial Institutions that resulted in the theft of millions of dollars from more than 800,000 victim bank accounts. One of the hackers and several other undiscovered criminals, were also charged with the stealing and selling of at least 160 million credit and debit card numbers, resulting in losses of hundreds of millions of dollars. According to the indictment, these losses included $300 million in losses for just three of the corporate victims not to mention the immeasurable losses to the identity theft victims, due to the costs associated with stolen identities and fraudulent charges.
Underground Prices for Stolen Credentials and Hacker Services
| Hacker Credentials and Services | Details | Price |
| *Visa and Master Card (US) | $4 | |
| American Express (US) | $7 | |
| Discover Card with (US) | $8 | |
| Visa and Master Card (UK, Aus & Can) | $7 -$8 | |
| American Express (UK, Aus & Can) | $12- $13 | |
| Discover Card (Aus & Can) | $12 | |
| Visa and Master Card (EU and Asia) | $15 | |
| Discover and American Express Card (EU and Asia) | $18 | |
| Credit Card with Track 1 and 2 Data (US) | Track 1 and 2 Data is information which is contained in digital format on the magnetic stripe embedded in the backside of the credit card. Some payment cards store data in chips embedded on the front side. The magnetic stripe or chip holds information such as the Primary Account Number, Expiration Date, Card holder name, plus other sensitive data for authentication and authorization. | $12 |
| Credit Card with Track 1 and 2 Data (UK, Aus & Can) | $19-$20 | |
| Credit Card with Track 1 and 2 Data (EU, Asia) | $28 | |
| US Fullz | Fullz is a dossier of credentials for an individual, which also include Personal Identifiable Information (PII), which can be used to commit identity theft and fraud. Fullz usually include: Full name, address, phone numbers, email addresses (with passwords), date of birth, SSN or Employee ID Number (EIN), one or more of: bank account information (account & routing numbers, account type), online banking credentials (varying degrees of completeness), or credit card information (including full track2 data and any associated PINs). | $25 |
| Fullz (UK, Australia, Canada, EU, Asia) | $30-$40 | |
| VBV(US) | Verified by Visa works to confirm an online shopper’s identity in real time by requiring an additional password or other data to help ensure that no one but the cardholder can use their Visa card online. | $10 |
| VBV (UK, Aus, Can, EU, Asia) | $17-$25 | |
| DOB (US) | Date of Birth | $11 |
| DOB(UK, Aus, Can, EU, Asia) | $15-$25 | |
| Bank Acct. with $70,000-$150,000 | Bank account number and online credentials (username/password). Price depends on banking institution. | $300 and less |
| Infected Computers | 1,000 | $20 |
| Infected Computers | 5,000 | $90 |
| Infected Computers | 10,000 | $160 |
| Infected Computers | 15,000 | $250 |
| Remote Access Trojan(RAT) | $50-$250 | |
| Add-On Services to RATs | Includes set up of C2 Server, adding FUD to RAT, infecting victim | $20-$50 |
| Sweet Orange Exploit Kit Leasing Fees | $450 a week/$1800 a month | |
| Hacking Website; stealing data | Price depends on reputation of hacker | $100-$300 |
| DDoS Attacks | Distributed Denial of Service (DDoS) Attacks– throwing so much traffic at a website, it takes it offline | Per hour-$3-$5 Per Day-$90-$100 Per Week-$400-$600 |
| Doxing | When a hacker is hired to get all the information they can about a target victim, via social engineering and/or infecting them with an information-stealing trojan. | $25-$100 |
*Note: All Credit Cards sold with CVV Codes
As always, there is no shortage of stolen credit cards, personal identities, known as Fullz, for sale. However, the hackers have come to realize that merely having a credit card number and corresponding CVV code is not always enough to meet the security protocols of some retailers. Hackers are also selling cardholders’ Date of Birth and other personal information. Having this additional information would allow a hacker to answer additional security questions or produce a fake identification, to go along with a duplicate credit card. VBV (Verified by Visa) data is also being sold.
It has been found that credit cards and personal identities for non-US residents continue to sell for more money than the credit cards and identities for US residents. An example of the pricing discovered for stolen credit cards, Track 1 and 2 Data of Credit Cards, Fullz, Date of Birth and VBVs for cardholders is listed in the table above.
Online Bank Accounts for Sale: Name Your Bank and Country Preference
Just as with stolen credit cards, there are hundreds of online banking credentials for sale. It has found that one can purchase the username and password for an online bank account with a balance between $70,000 and $150,000 for $300 and less, depending on which banking institution the account is located. Also one can specify the login information for an account within a specific bank and country.
Malware Infected Computers for Sale
There are thousands of compromised computers (bots) for sale by bot salesmen. The price per computer typically decreases when they are bought in bulk. The costs for infected computers (bots):
- 1,000 bots = $20
- 5,000 bots= $90
- 10,000 bots = $160
- 15,000 bots = $250
Infected computers in Asia tend to sell for less. It is thought that infected computers in Europe & U.S. are more valuable than those in Asia, because they have a faster and more reliable Internet connection.
Once scammers buy the malware-infected computers, they can do anything they want with the machines. They can harvest them for financial credentials, infect them with ransomware so as to extort money from their owners, or use them to form a spam botnet to send out malicious spam on behalf of other scammers. If you don’t think there is much money in the spam business think again. Research into one of the largest spam botnets, Cutwail, it is estimated that the Cutwail gang’s profit for providing spam services was approximately $1.7 million to $4.2 million over two years.
Malware and Exploit Kits for Sale
A variety of Remote Access Trojans (RATs) are for sale ranging from $50 to $250. Most of the RATs are sold with a program to make it Fully Undetectable (FUD) to anti-virus and anti-malware. However, there were some hackers who sold the FUD component for an additional $20. For those RAT buyers who want the seller to do all the work for them, eg: setting up the RAT’s Command and Control Server, configure the malware to be FUD and possibly infect the target, they could pay an additional $20 to $50.
Exploit Kits – One of the offerings the Sweet Orange Exploit Kit for lease charged between $450/week and $1800/month. Sweet Orange is certainly more expensive to lease than the once popular BlackHole Exploit kit. Before BlackHole’s supposed creator was arrested, the leasing rates for BlackHole were:
- 3 months—$700
- 6 months–$1,000
- One year–$1,500
Hacker Services for Hire: DDoS Attacks, Hacking of Websites, Doxing
Hacking into a Website
The cost to hire a hacker to break into an organization’s website runs between $100 – $300. Generally the higher the fee, the more reputable the hacker. What is worth noting is that most hackers for hire will not hack into a government or military website.
Distributed Denial of Service (DDoS) Attacks
A DDoS is where 1000’s of computers, controlled by a RAT, are used to attack a website and bring it to a halt through sheer volume of traffic. Those customers wanting to purchase DDoS Attack Services could pay by the hour, day or week. Most hackers who provide the DDOS attacks guaranteed that the target website would be knocked offline.
The rates were as follows:
- DDoS Attacks Per hour = $3-$5
- DDoS Attacks Per Day = $90-$100
- DDoS Attacks per Week = $400-600
Doxing
Doxing is when a hacker is hired to get all the information they can about a target victim. Their methods include searching public information sites, social media sites, as well as manipulating the victim via social engineering and infecting them with an information-stealing Trojan. There are a lot of Doxing services for sale on the hacker underground, A “Vouch” from customers is used to verify that the hacker providing the Doxing service is legitimate. Doxing services range from $25 to $100.
Name Brand Products, Get Them For Cheap
Another service being sold on the hacker underground is where hackers will sell popular products, below the retail price. The hackers will obtain a specified product for a buyer either by using a stolen credit card or by working a scam, where they contact the retailer’s customer service representative and pretend to have purchased the item from the vendor, and it was damaged. The customer service representative is convinced that the complaint is legitimate, and they send out a replacement to the scammer, who in turn sells the product below the retail price.
Summary
For the most part, it does not appear that the types of hacker services and stolen data for sell on the hacker underground have changed dramatically in the past several years. The only noticeable difference is the drop in price for online bank account credentials and the drop in price for Fullz or Personal Credentials. In 2011, hackers were selling US bank account credentials with balances of $7,000 for $300. Now, accounts with balances ranging from $70,000 to $150,000 go for $300 and less, depending on the banking institution where the account is located. In 2011, hackers were selling Fullz for anywhere from $40 to $60, depending on the victim’s country of residence. Fullz are now selling between $25 and only go up to $40, depending on the victim’s location. It is believed that the drop in prices further substantiates that there is an abundance of stolen bank account credentials and personal identities for sale. There is also no shortage of hackers willing to do just about anything, computer related, for money, and they are continually finding ways to monetize personal and business data.
Key Protective Security Steps
Companies should adopt a layered approach to security and consider implementing the following:
- Firewalls around your network and Web applications
- Intrusion Prevention Systems or Intrusion Detection Systems (IPS/IDS). These inspect inbound and outbound traffic for cyber threats and detect and/or block those threats
- Host Intrusion Prevention Systems (IPS)
- Advanced Malware Protection Solution
- Vulnerability scanning
- 24 hours a day x7 days a week x365 days a year log monitoring, and Web application and network scanning
- Security Intelligence around the latest threats (people working on the latest threats in real-time, human intelligence)
- Encrypted email
- Educating your Employees on Computer Security. A key protective measure is to educate your employees to never click on links or attachments in emails, even if they know the sender. Employees should check with the sender prior to clicking on the email links or attachments. Client side attacks using email attachments and hyperlinks to malicious code on the web are the two major infection vectors.
The good news for SME’s is that there are some products out there that are open source and free that can cover a lot of the above. Configured correctly will help to protect the network from malicious hackers, at least make them want to bypass you and attack an easier target.
Individuals Should Implement the Following Security Steps
- Computer users should use a computer dedicated only to doing their online banking and bill pay. That computer or virtualized desktop should not be used to send and receive emails or surf the web, since Web exploits and malicious email are two of the key malware infection vectors.
- Avoid clicking on links or attachments within emails from untrusted sources. Even if you recognize the sender, you should confirm that the sender has sent the specific email to them before clicking on any links or attachments.
- Reconcile your banking statements on a regular basis with online banking and/or credit card activity to identify potential anomalous transactions that may indicate account takeover.
- Make sure your anti-virus is current and can protect against the latest exploits. Also, make sure that your anti-virus vendor has signatures for detecting the latest Trojans and that you have the most up- to-date anti-virus protections installed.
- Do not use “trial versions” of anti-virus products as your source of protection. Trial versions of anti-virus products are good for testing products, but do not continue to use the trial version as your protection for your home or work PC. The danger is that the trial version does not receive any updates, so any new Trojan or virus that is introduced after the trial version was released will have total access to your PC.
- Make sure you have your security protections in place. Patch management is key. It is critical that as soon as they become available you install updates for your applications and for your computer’s operating system.
- Be cautious about installing software (especially software that is too good to be true – e.g., download accelerators, spyware removal tools), and be conscience about pop-ups from websites asking users to download/execute/or run otherwise privileged operations. Often this free software and these pop-ups have malware embedded.
Make sure your company is not an easy target for the cyber criminals by having a penetration test by a trained and experienced Certified Ethical Hacker.
Penetration testing is the process of evaluating both your physical and digital security systems and finding all areas that are insecure and that need attention. The main goal of penetration testing is not only to find security vulnerabilities, but to attempt to exploit them as well, which can decrease the chances of data loss or allowing unauthorised persons access to secured data. Common problems discovered by penetration testing include software bugs, design flaws and configuration errors. Once these have been identified, they need to be quickly repaired in order to ensure that safety isn’t compromised for longer than necessary. Testing is vital for any business, no matter how large or small, as data has become the most important currency available to organisations and hackers.
Penetration testing should be performed by an experienced tester from outside the organisation or the service provider whom has configured the solution, website, network, etc. It is all too easy to ignore or turn a blind eye to a known issue, or to have the attitude of ‘Nobody could possibly find that flaw!’ or ‘Who would want to hack us? We’re not interesting enough!’ As this involves the security of the business, no half-measures can be taken. Security breaches happen every minute of every day, and unless you have a dedicated team for penetration testing, it may be wise to consider outsourcing the procedure. Having an in-house team is ideal, but there are many businesses that find good reasons to outsource the testing and security of their information systems.
Thanks to our Guest blogger this month
Wynn Jones ECSA/LPT CEH CHFI CVE CCA MCSE
http://www.praetoriansecurity.co.uk
Is Virus Protection enough anymore?
 I thought I would burp a little about the recent news broadcasts detailing the attacks that have happened, as well as the ones that are about to hit in around two weeks’ time.
I thought I would burp a little about the recent news broadcasts detailing the attacks that have happened, as well as the ones that are about to hit in around two weeks’ time.
Let’s start with the one that already happened, the Heart bleed exploit. This affected web servers and took advantage of a flaw in a commonly used library to gather random chunks of working memory. Unfortunately these random chunks often contained people’s login details or other personal information. And so we all had to go and change our passwords for many of the web services we use, Google, Facebook, and Yahoo and so on. Wait, you haven’t done that yet? Well you better get in about it today and make it so!
The attack due in a few weeks’ time was announced on the news feeds last week, and you need to make sure that all your computers are up to date and virus protected within the next two weeks. You have been warned!
So what’s new?
Well, in actuality, nothing is new. We have been plagued with hackers, attacks, and viruses for as long as I have been in IT. And there is even a possibly they were around before then, I am not as old as you think you know! We have long been advised to keep our computers up to date, to install virus checking software and ensure we have the latest virus definitions. Yet we still succumb to the viruses as they hit the web. Is it because we just get lazy and don’t maintain our computers? Has the computer age made us feel that the software should maintain itself? Why do we have to do anything manually?
I have repaired machines in the past, and have asked the user if they had anti-virus software. The answer was often yes, as it came with the computer. Brilliant I said have you updated it recently … a long pause … no, was the reply, doesn’t it do that itself? I then checked the machine to find that the software was on it when bought, but had never been launched and never registered. In fact, it had simply been taking up some hard drive space and doing not a lot else! Given this was roughly three or four years after purchase, I will not tell you the number of infections I found on that machine.
Which hat are they wearing?
These days you can attend college or university and do an Ethical Hacking course, and come out with a matching qualification. Now if you use this the right way (known as white hat hacking) you will become an asset to any company wanting to protect their systems. Of course, used the wrong way (black hat hacking), you can cause mayhem and leave damage in your wake.
Help me Ian; what do I need to do?
Put simply, you need to do what you have been told to do for as long as I can remember. That is: keep your computer up to date, and keep anti-virus software on it and up to date. If you are on a network, then make sure your firewalls and other barriers are up and running. Oh, and just to let you know, it could all be changing again as the mobile usage increases and the cloud becomes our storage … watch this space, but be protected.
Further info on some of this can be gained by reading our previous blog on Windows XP cover, and on Passwords security.
Take care and be safe…
Let us know your thoughts on this issue and how you are coping in the battle for safe working.
Sniffing Around CES2014 in Vegas!
I have always wanted to put that as a title. However sadly we are not at CES 2014 in Vegas but we are sniffing around some of the reports that are appearing online to see what is being displayed and demoed this year.
The news if heavy with all sorts of reports from all our favourite electrical companies, Samsung stealing a lot of the press with their Ativ Book 9 2014 edition and of course their curved televisions 50-inch OLED.
LG have released their curved phones, which use OLED technology. They have also been showing off their Fireweb Firefox driven phone and not to be left out of course have launched and showed of their 4K curved OLED TV, 77-inch in size with a picture that is stunning.
Sony is producing facts and figures about sales of the new PS4 against the Xbox One and it looks like Sony is in the lead now and if the figures are to be believed, well in front.
Other news, is that Android devices are to top 1 billion in 2014, so not much slow down there.
One of the most interesting facts is that there are more wearable devices than ever before and a lot of talk about Intel moving in this direction. This is firing up rumours that Intel might be giving up on its mobile ambitions to pursue the wearable market. Time will tell.
Lenovo are still prominent this year with their Lenovo Thinkpad 8, they claim this newest offering, “will put a full PC in the palm of your hands.”
Other memorable news feeds are talking about the progress of self-driving vehicles, again this technology is developing fast and the computers are now able to handle more data than ever before, so watch out for the self-driving vehicle coming your way soon, no pun intended.
I will leave you with this link to a 3D food printer that has appeared at CES this year, it prints chocolate and candy….now there’s a printer for the office……
Yes, CES 2014 has once again not let any of us GEEKS down. There are developments from the hardware manufacturers like Tegra and snapdragon showing off where things are going next right down to new travel experiences and viewing delights.
Check out some of the feeds online and start to get excited about what is happening in the world of tech.
What would you like to see come sooner rather than later, let us know?
Ian Thomson
IT Turning Point
Flexible screens, a touch of the future?
The rumours and sneak previews of flexible screens by Samsung and other manufacturers has caught our eye and intrigued is. So here we are going to give you some gleaned info from the net.
But first let us ask you a question. What usage would you see flexible screens having and would they be better than what we have just now?
We picked our brains and thought of some of the following: –
Wrist devices.
Jackets or waist coats.
Wall mounted devices that follow the contours of the wall.
But what else?
Anyhow, onto what we have gleaned from the web.
We have viewed over the last 8 to 10 months the videos that have been going around demoing the flexible screen, or OLED manufacture. This new revolution has made manufacturers like Samsung go into overdrive with concept devices and then create videos demoing what they might look like. Here is one we have seen a few times and gets you thinking.
Samsung showed this at their CES talk this year. A brief potential view of where this technology maybe taking us. Again it will be down to the patent race and who gets the patents in first. Watch this space.
This next video shows the durability of the new screen technology, WARNING it does hurt to watch the screens we love today being pounded by a hammer…..
Ouch, that’s just not nice. But what about the OLED screen, durability at its core, flexible and will take abuse. There is definitely a market for that.
How about a touch window in your house. You get up in the morning and draw the curtains and the blinds are built into the window. Then you call up all sorts of touch screen info about weather and driving conditions etc. You are kidding me Ian surely I hear you cry….Well no.
Isn’t that amazing? Come on, it had you excited…..
So it looks like we will be able to wear the flexible units with Samsung already having launched their wrist device that is curved. We will also be able to drop then of a building by the look of it and then our houses will be equipped with the latest tech and info.
I just can’t wait!
Samsung are not the only manufacturer by the way, it is just they are at this time shouting the loudest about it with videos and promotions.
What are your thoughts on all this new Flexible screens and tech, does it excite you or bore you?
Ian Thomson
Consultant
IT Turning Point
Windows 8 is on the shelves, will you change?
 Microsoft have launched the latest incarnation of the Windows operating system and it’ s again a major revamp to tap into the mobile tablet market, where they have been lagging behind for some time.
Microsoft have launched the latest incarnation of the Windows operating system and it’ s again a major revamp to tap into the mobile tablet market, where they have been lagging behind for some time.
Is it too little too late? Well that remains to be seen, they still have 2.5 billion desktop users worldwide and they have to be maintained and brought into the next operating system. This proved hard with Widows Vista where less that 30 % adopted the new operating system. Windows 7 redeemed them slightly and has now been adopted widely and clients and enterprise networks moving into Windows 7 with gusto now. Of course this was on the back of Microsoft dropping Windows XP, by far best incarnation so far and the one that just runs and runs.
So what of Windows 8?
Well it is a change again from what we are all used to and is designed primarily to attack the tablet market and mobile devices. The Start menu has changed and the desktop layout is completely changed.
In the main guts of it the system itself has changed, better power usage, more difficult to hack, faster to boot up as it leaves some of the operating system on a hard drive space in a memory slot so it can boot quicker, similar to the hibernation system we have had in Windows for some time and it works. There will be the inevitable learning curve and complaints about where everything now can be found. But that’s progression for you.
Adoption
As usual we predict that the larger organisations will stay with an older version of the operating system until Windows 8 has been proven and the first or even second service pack is launched.
This is always the case and nothing new for Microsoft. The biggest up take will be home users and the new computer purchases, which will drive the sales forward. Also the launch of Microsoft Surface, which is another name for the Windows 8 on a tablet. So the tablet market may take off big time. So look out for bargains of the older stock that retailers will get rid of.
Will you change?
Well it is this author’s opinion that it is a personal matter of the individual user as to when you change; just make sure that all your existing apps will work with Windows 8.
For companies it is always advisable to wait for the fixes to hit before adoption on a large scale.
Check out the buzz on the Internet now about Windows 8 and read as much as you can before you believe all the hype and take that plunge.
Good luck.
Ian Thomson
Founder/Senior Trainer/Consultant